Equiti Login
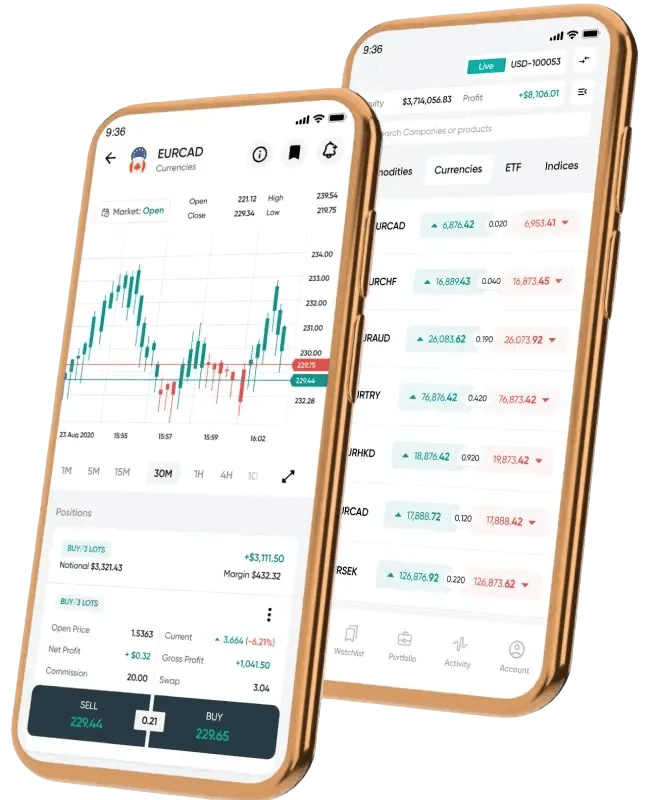
Secure Login System Overview
Equiti provides Egyptian traders with a multi-layered secure login system across all trading platforms and the client portal. The authentication infrastructure processes over 100,000 daily login requests through encrypted channels. Advanced security protocols protect account access through multiple verification steps. The system maintains 256-bit SSL encryption for all data transmission. Real-time monitoring detects and prevents unauthorized access attempts. Biometric authentication options enhance security on mobile devices. Regular security audits ensure protection against emerging threats.
Login Methods Comparison:
| Platform | Authentication Options | Security Features | Session Duration |
| Client Portal | Email/Password, 2FA | IP Tracking, SSL | 30 minutes |
| MT4/MT5 | Investor/Trading Password | Data Encryption | 24 hours |
| Equiti Trader | Biometric, PIN, 2FA | Device Recognition | 12 hours |
| WebTrader | Email/Password, 2FA | Session Monitoring | 8 hours |
Client Portal Access Features
The Equiti client portal serves as the central hub for account management in Egypt. Traders access their accounts through unique credentials verified against encrypted databases. The portal implements automatic timeout features after 30 minutes of inactivity. Security systems track login locations and flag suspicious access patterns. Password requirements enforce complex combinations of characters and regular updates. Account recovery procedures involve multiple verification steps. The system maintains detailed access logs for security auditing.
Security Authentication Steps
Portal login security includes:
- Two-factor authentication
- Device recognition systems
- IP address validation
- Session monitoring
- Automatic timeout features
- Failed attempt limiting
- Real-time notifications
MetaTrader Platform Login Process
MT4 and MT5 platforms utilize separate login credentials for added security. Trading servers validate access requests through encrypted channels. The platforms support both trading and investor passwords with different permission levels. Automatic login features maintain security while providing convenient access. Session management tools monitor active connections and terminate suspicious activities. Password encryption prevents unauthorized credential access. The system enforces regular password updates for enhanced security.
Authentication Methods Overview:
| Method | Security Level | Recovery Time | Availability |
| Standard Login | Basic | Immediate | All Platforms |
| 2FA | Enhanced | 1-2 minutes | Portal/Mobile |
| Biometric | Maximum | Instant | Mobile Only |
| SMS Verification | High | 1-5 minutes | All Platforms |
| Email Token | Enhanced | 2-10 minutes | Portal/Web |
Mobile Application Security
Equiti Trader app implements advanced security measures for Egyptian mobile users. Biometric authentication options include fingerprint and facial recognition. The application maintains encrypted local storage for login credentials. Device binding prevents unauthorized access from unknown devices. Push notifications alert users to login attempts from new locations. The system supports offline authentication through secure tokens. Regular security updates protect against mobile-specific threats.
Mobile Security Features
- Biometric authentication
- Device fingerprinting
- Secure credential storage
- Location-based alerts
- Automatic session management
- Encrypted communication
- Remote device deauthorization
Password Management Systems
The platform enforces strict password policies protecting Egyptian trading accounts. Password requirements include minimum length and complexity standards. The system maintains encrypted password storage using advanced hashing algorithms. Regular password change requirements prevent credential compromise. Password recovery procedures involve multiple verification steps. The platform prevents use of previously compromised passwords. Historical password databases protect against unauthorized reuse.
Two-Factor Authentication Implementation
Egyptian traders benefit from robust two-factor authentication across all platforms. The system generates time-based one-time passwords through secure algorithms. Multiple 2FA methods include SMS, email, and authenticator apps. Backup codes provide access when primary 2FA methods are unavailable. The platform supports hardware security keys for enhanced protection. Authentication attempts are logged and monitored for suspicious patterns. Recovery procedures require identity verification through multiple channels.
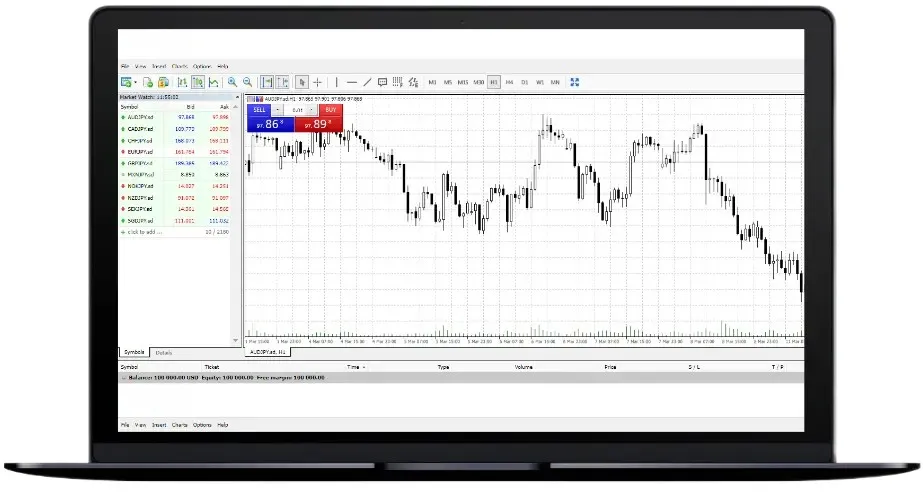
2FA Options Available
The system supports various 2FA methods:
- Google Authenticator
- SMS verification codes
- Email authentication
- Hardware security keys
- Backup recovery codes
- Biometric verification
- Time-based tokens
Session Management Controls
Equiti implements comprehensive session management across trading platforms for Egyptian users. Automatic timeout features terminate inactive sessions after predetermined periods. The system tracks concurrent login attempts and restricts multiple sessions. IP-based access controls prevent unauthorized location access. Session monitoring detects unusual trading patterns or access attempts. Forced logout features protect accounts during suspicious activities. Administrative tools enable remote session termination when required.
Login Security Metrics:
| Security Feature | Standard Account | Premium Account |
| Session Timeout | 30 minutes | 60 minutes |
| Failed Attempts | 5 per hour | 10 per hour |
| Password Length | 8 characters | 12 characters |
| 2FA Methods | 2 options | All options |
| Device Limits | 3 devices | 5 devices |
Account Recovery Procedures
Equiti maintains stringent account recovery protocols for Egyptian traders requiring access restoration. The recovery process involves multiple verification layers including government ID validation and security questions. Recovery requests trigger immediate account security holds preventing unauthorized transactions. Support teams process recovery requests within four hours during Egyptian business hours. The system requires updated contact information verification before access restoration. Account history reviews identify potential security compromises during the recovery period. Security protocols implement new authentication measures after successful recovery.
FAQ:
2FA requires verification through a secondary method after password entry, using time-based codes generated through authenticator apps, SMS, or email.
The password recovery process requires email verification, identity confirmation, and possibly contact with support for enhanced security measures.
Account access is limited to a specific number of devices based on account type, with Premium accounts allowing up to 5 concurrent device connections.